What Is Token Ring
Token ring network is a popular local area network (LAN) technology, which is developed by IBM. It can send data in one direction to a certain number of locations through a token. Token ring topology provides a mechanism for ring failover operation.
Besides, token ring embeds the management to constantly supervise and control the ring. This job is conducted by a designated station on the ring, which is known as the active monitor chosen based on a claim token process. The active monitor solves certain error conditions that may take place on the ring like lost tokens/frames and clocking errors.
Token ring was standardized in the IEEE802.5 specifications, which describe the execution of a token-passing ring network configured as a physical star topology. Token ring utilizes a special three-byte frame called a token that goes through a logical ring of workstations or servers.
This token passing is a channel access method that offers fair access to all stations and reducing the collisions of tradition-based access methods. Though token ring has been greatly outpaced by Ethernet in recent years, it still has a huge installed base.
Also see: What Is NetBIOS (Network Basic Input/Output System)
The Development of Token Ring
In the early 1970s, various kinds of local area network technologies were developed. The Cambridge Ring was one of these technologies, which showed the potential of a token passing ring topology. Plenty of teams in the world started working on their own implements.
Among them, the development of IBM’s Token Ring technology is particularly outstanding. The early work led to the Proteon 10Mbit/s ProNet-10 Token Ring network in 1981. Later on, Proteon developed a 16 Mbit/s version running on unshielded twisted pair cable.
On October 15, 1985, IBM released their own proprietary Token Ring product, which ran at the speed of 4 Mbit/s. Devices like INM computers, midrange computers, and mainframes can connect to it. The faster 16 Mbit/s Token Ring was standardized by the 802.5 group in 1988. Then an increase to 100 Mbit/s was standardized and marketed in the wane of Token Ring.
Since the release of 1000 Mbit/s standard in 2001, no products were brought to the market. With the development of Fast Ethernet and Gigabit Ethernet, the standards activity of token ring came to a standstill.
Recommended article: What Is DHCP (Dynamic Host Configuration Protocol) Meaning
How Does Token Ring Work
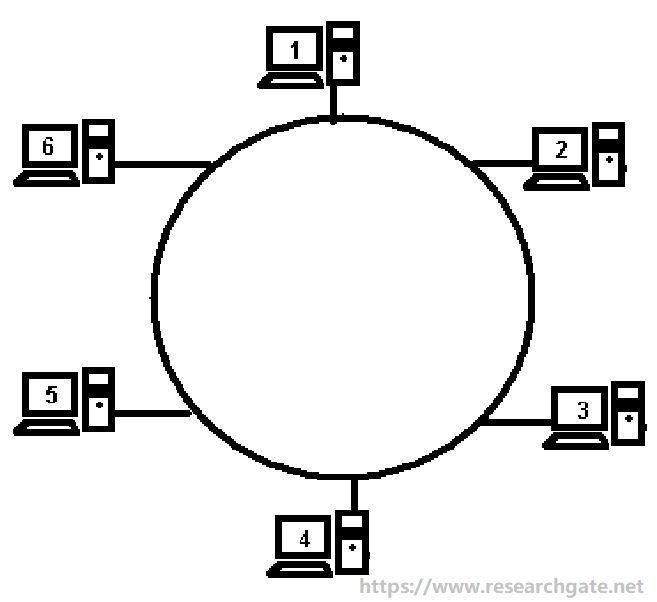
Learning the working theory of token ring helps you obtain a further understanding of token ring networking. Systems in the same LAN usually are arranged in a logical ring. Each system receives data frames from its logical predecessor on the ring and sends them back to its logical successor.
The network might be an actual ring that has cables directly connecting each node to its neighbors. But in most cases, the network is a star with the ring existing only logically in the wiring closet in the “multiaccess unit” to which all the hosts connect.
Empty information frames are circulated on the ring in a continuous way, together with frames including actual data. You need to note the fact that any node receiving an empty frame and having nothing to send forwards the empty frame.
A computer will wait for an empty frame to send a message. If it has one, it will insert a token implying that it is sending data in the frame. In addition, your device will insert the data it plans to transmit into the payload section of the frame and then set a destination identifier on the frame.
When a computer knows it can’t transmit its own data, it will do the following things. If it is not the sender or the destination, it just retransmits the frame. You can send it to the next host in the ring.
If the computer is the sender, it sees that the message has been received, removes the message payload from the frame, and sends the empty frame around the ring. If this computer is the destination for the message, it will copy the message from the frame and erase the token to imply receipt.
This post has illustrated what tokenring network is for you. Moreover, it shows you the development and working principle of token ring.