Malware is designed to damage your computer systems and there are different types of malware. This post from MiniTool provides detailed information about the types of malware. Besides, there are some useful tips for you to avoid malware. Now, keep on your reading.
What Is Malware
What is Malware? Malware is software designed to damage computers and computer systems. It is used to bypass access control to damage computer functions, and steal data. In short, malware is a piece of software designed to damage computers, tablets, phones, computer systems, networks.
Malware can cause damage and destruction to your organization. Some people may ask “what are the 4 types of malware” or “what are 5 types of malware”. Actually, there are many types of malware and they are increasing every day. Now, let’s see some common types of malware.
The 9 Common Types of Malware
- Virus
- Worm
- Adware
- Spyware
- Malvertising
- Ransomware
- Hybrids
- Trojan Horse
- Bots
Types of Malware
1. Virus
The virus is one of the most common types of malware. The virus is designed to destroy its target computer by destroying data, reformatting the hard drive, or completely shutting down the system. They can also be used to steal information, create botnets, steal money, provide advertisements, destroy computers and networks, etc.
When you run infected programs, viruses can attach themselves to programs and execute code to copy themselves and spread to other computers. Computer viruses require human intervention to spread to other computers and are usually spread via email attachments and Internet downloads.
2. Worm
Worms are the most common type of malware, which uses operating system vulnerabilities to spread in computer networks. The worm can be more destructive than other types of malware since it is a standalone program that can copy itself to infect other computers.
They can quickly infect a large number of computers, consume bandwidth, and overload the webserver. They can also encrypt data for ransomware attacks, steal information, delete files, and create botnets.
3. Adware
Have you ever noticed an ad suddenly appeared on your computer? This may be adware. Adware is a type of malware that causes ads to be displayed on your computer and it can generate revenue for ad creators.
It is usually displayed in the form of pop-up advertisements or advertisements embedded in software or programs. Adware can also provide spyware and is usually easily hacked. To know if you have been hacked, this post – How to Know and What to Do If You Have Been Hacked is what you need.
4. Spyware
Spyware is installed on your computer without your permission and is designed to track your browsing habits and Internet activity. When hackers use spyware, they can access any type of sensitive information of yours.
Spyware can be spread by exploiting software vulnerabilities, bundling with legitimate software or Trojan horses. It is commonly used for identity theft and credit card fraud. Although spyware is dangerous, fortunately, it is easy to remove.
5. Malvertising
Malvertising is not the same as adware. Legitimate advertisements will be attacked by malware through malvertising, and then the malware will be sent to the target computer. Cybercriminals may place ads on legitimate websites. When you click the ad, the code in the ad will redirect you to a malicious website or install malware on your computer.
6. Ransomware
Ransomware is a type of malware that can capture your data and demand payment to release it back to you. It encrypts files on the hard drive or locks the system and displays messages. It aims to force you to pay the attacker to release restrictions and regain access to the computer. After paying the attacker, your system and data will be restored to their original state.
There are two general types of ransomware to notice. The first is the locker ransomware, which restricts access to the computer or infected device. The second is the crypto ransomware, which restricts access to files and stored data.
7. Hybrids
Malware is also a combination of two different types of attacks. This usually means combining worms or Trojan horses with malware or adware. That is to say, the malware program appears to be a Trojan horse to you, but once executed, it will attack other victims over the network like a worm.
To remove these types of malware attacks, you must start with anti-malware scanning and remove the control components from memory.
8. Trojan Horse
Trojan horses pretend to be normal, harmless files or programs that enter your system to trick you into downloading and installing malware. Once you have installed a Trojan horse, cybercriminals will access to your system.
The most popular type of Trojan is a fake antivirus program that will pop up and claim that you have been infected, and then instruct you to run the program to clean your PC. It’s hard to defend against Trojan horses.
Also see: WARNING: 250 Million Account Trojan Can Disable Windows Defender
9. Bots
A zombie program is a computer infected with malware, so hackers can control it remotely. The zombie program can then be used to launch more attacks or become part of the zombie program collection. Botnets can spread millions of devices because they will not be discovered.
Botnets can help hackers carry out various forms of malicious activities, such as DDoS attacks; keyloggers, screenshots, and webcam access; send spam and phishing emails; spread other types of malware.
Also see: 7 Best Recommended Webcam Recording Software in 2020
How to Find and Remove Malware
Just now, you have known the different types of malware. Then, you may wonder how to find and remove the malware. If you notice the following signs, your computer may be infected by the malware.
- BSOD (Blue screen of death).
- Lack of storage space.
- The computer is slow, crashing, or freezing.
- The program opens or closes or changes by itself automatically.
- Send emails and messages without prompting.
- There are some pop-up windows, toolbars, and other unwanted programs.
How to Avoid the Different Types of Malware
Then, I will introduce how to avoid different types of malware.
- Never open, click or download content that you think is too suspicious, such as files, advertisements, emails, etc.
- Install a firewall that can be used to detect any suspicious activity. Maybe, you are interested in this post –Windows Firewall for Windows 10 and Its Great Alternative.
- Purchase, run, and regularly update anti-malware and anti-spyware software.
- Only connect to a secure Wi-Fi network. Connecting to public Wi-Fi may expose your network to potential harm.
- Update the operating system regularly.
- Install spam filters to prevent the possibility of infection on all devices.
- Change your password regularly and follow password best practices.
- Use a secure file sharing solution. This post – Top 8 File Sharing Programs Windows 10 [2020 Update] is what you need.
- Back up your important data regularly.
Back up Your Data to Protect the PC
Speaking of backing up data, there is a great backup software – MiniTool ShadowMaker for you. It is also a powerful tool to protect your Windows. It is an all-around and free backup software designed for Windows 10/8/7, providing you with a data protection & disaster recovery solution.
Besides backing up the system, this software can also be used to back up files, folders as well as the partitions. It is also a clone tool that can help you to clone the OS from HDD to SSD without data loss. So, besides creating a system image, you can also choose to clone the OS disk to another hard drive to get the Windows system without reinstalling.
MiniTool ShadowMaker also supports restore Windows backup to a different PC with dissimilar hardware. This post – How Can You Do Windows Backup Restore to Different Computer can help you do that.
Now you can download and try MiniTool ShadowMaker Trial Edition to do the backup task.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Let’s see how to use MiniTool ShadowMaker to back up your files.
Step 1: Decide a Backup Mode
- Launch MiniTool ShadowMaker.
- Continue to use the trial edition by clicking Keep Trial.
- Choose This computer to continue by clicking the Connect button.
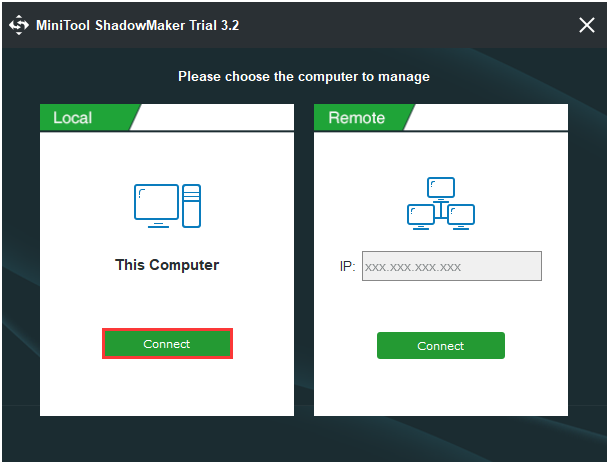
Step 2: Choose the Backup Source
- Under the Backup page, click Source to choose the backup type – Folders and Files.
- Select the files you need to back up and click OK.
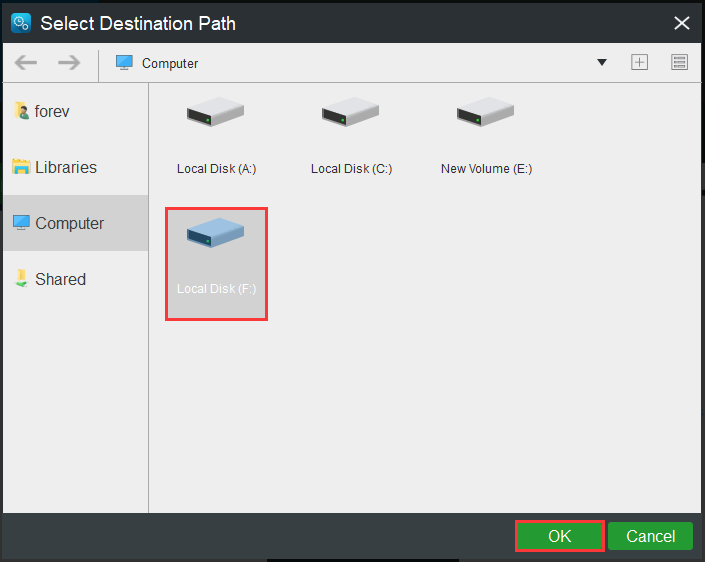
Step 3: Choose a Destination Path
- Click the Destination tab.
- Choose one partition to store your files based on your needs and click OK.
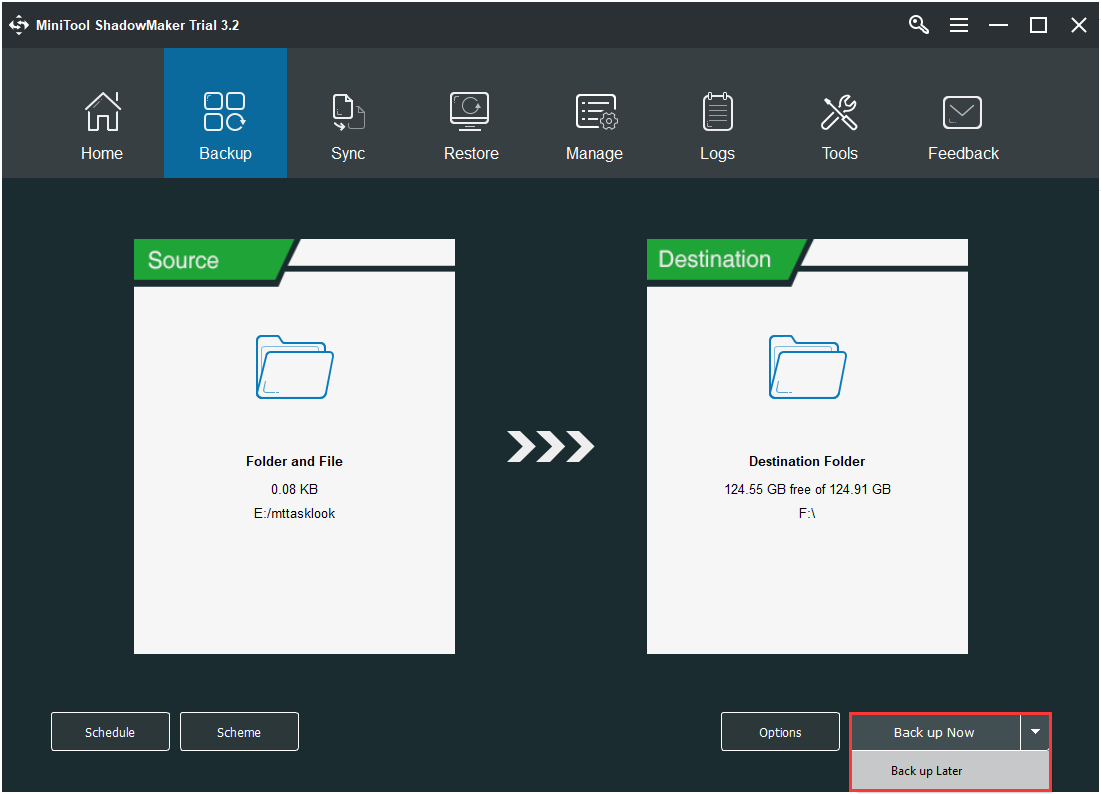
Step 4: Start the Backup Process
- Go back to the previous interface.
- Click Back up Now to start the process immediately or choose Back up Later to delay the backup task.
Now, you have backed up your important files successfully.
You can use another feature of MiniTool ShadowMaker to back up files: Sync. Here is how to sync files:
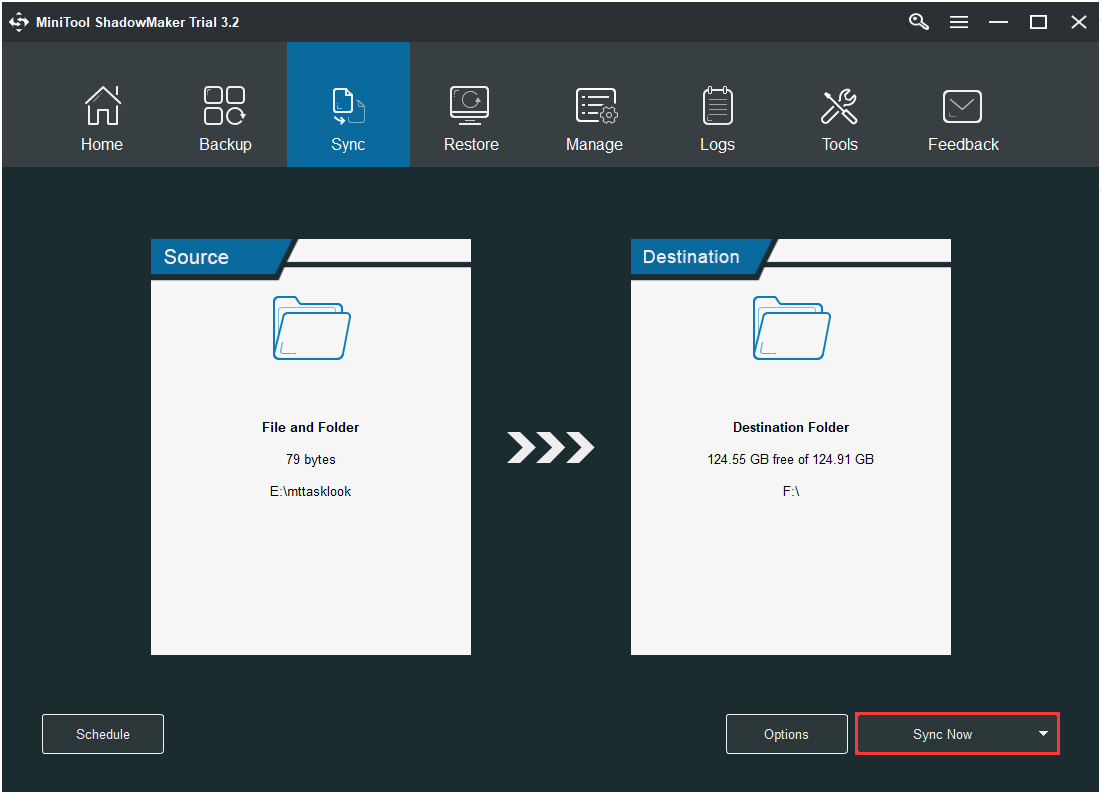
Step 1: After launching MiniTool ShadowMaker, go to the Sync page.
Step 2: Click the Source and Destination module to choose the files that you want to sync and the storage path.
Step 3: Click the Sync Now button to immediately perform the sync process.
Also see: 5 Useful Solutions to Sync Files Among Multiple Computers
Bottom Line
This post has briefly shown you some basic information about the types of malware and you can know how to avoid it. Besides, this post also introduces you to a powerful program – MiniTool ShadowMaker, which can help you back up data to protect it.
If you have any problems when you are using our program, please let us know. Or if you have any suggestions, also tell us. Sending an email to [email protected] or leaving a comment below is available.
Types of Malware FAQ
- Power off the phone and reboot.
- Uninstall the suspicious application.
- Install a robust mobile security app on your phone.
If you think your computer has been infected, you can follow the steps below to remove malware from Mac and Windows PC/laptop.
- Disconnect from the Internet.
- Enter Safe Mode.
- During the malware removal progress, you need to avoid logging into accounts.
- Check your activity monitor.
- Run a malware scanner.