In your daily life, you may use antimalware software to protect your computer. However, sometimes your computer is still invaded by malicious hackers and malware because they can change their tactics so that antimalware software can’t find them.
Then a question comes here – how to know if you have been hacked. The following are some hacking signs:
1. You can’t log into your account.
2. Your device is acting strangely.
3. Your webcam lights up when it is not in use.
4. Your browser is being rebellious.
5. A hacker tells you that they have compromised you.
6. Activity that wasn’t yours.
Now, I will introduce what should you do if you have been hacked. Keep on your reading.
What to Do If You Have Been Hacked
1. Wipe Devices and Perform a System Restore
Once you have determined that you have been hacked, the first thing you need to do is wiping your hard drive and performing a system restore since a compromised computer can never be fully trusted again.
If you have created a system restore point in advance, you can perform it now. Maybe this post – What Is System Restore Point and How to Create It Look Here is what you need. You can also try to reinstall the system to make sure that you have a clean system.
Then you can try the following advice below if you have received you have been hacked message.
2. Change Passwords
Hackers use the password to get access to your accounts and networks. Thus, you need to change your password is the easiest to prevent this situation from happening again. It’s not recommended to couple your email addresses with a weak password, such as “‘123456”.
If your passwords are too simple, a hacker requires minimal effort to gain access to your account. As well as complexity, make sure that they are never reused on multiple accounts, no matter how convenient, which is the key to effective secure passwords.
3. Turn on Two-Factor Authentication
If you have been hacked, you can try to turn on 2FA( two-factor authentication) for your Microsoft account. Once you turn it on, it’s more difficult for hackers to sign in, even if they have got your password.
You can set your phone number or an alternative email address to protect your Microsoft account. Here are the steps:
Step 1: Access your security settings on your Microsoft account.
Step 2: On the Security settings page, you should click Add security info.
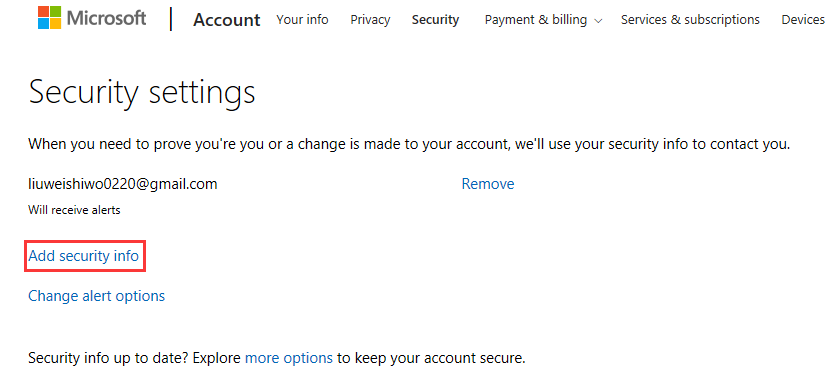
Step 3: You can choose A phone number or An alternative email address to verify your identity. Here we take the phone number as an example, and you should input your phone number and choose a way to verify the phone. You can choose Text or Call and click Next.
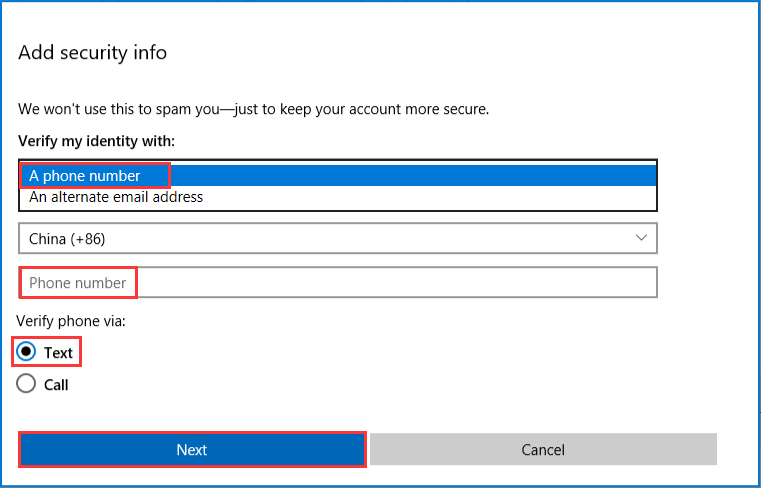
Step 4: Input the code you have received and click Next, then you have turned on 2FA.
4. Monitor Your Accounts
Attacks rarely stop on one account. If hackers have some success, they are likely to try to control other accounts. After you have been hacked, an attack on one area should always be considered a signal to double-check the security of others.
You should check your email to make sure they don’t use your account to forward information and make sure they don’t use social media accounts to contact people you follow.
Even if you lose control of your account, you can still restore it. For many major accounts, including those held by Google, Facebook, Twitter or Apple, there are account recovery tools or processes to prove your identity to make you regain control of the accounts.
5. Check Your Bank Statements
You should not only check the email and social media accounts. Pay attention to your transactions. The main reason for hackers invading Internet accounts is to make money. Once they get the information on your credit card, they will attempt to make purchases until that card is blocked.
If they can get into your PayPal account, your money will be transferred to an account they control.
After getting the “you have been hacked” message, you should immediately alert your bank or other financial institution. If you think your credit card details have been compromised, contact these institutions to cancel the card.
But keep your eyes on your bank accounts, just in case. You may not see anything for a few days since charges don’t always appear immediately.
6. De-Authorize Apps on Facebook, Twitter, Google, etc.
Some social media services allow you to link apps to your account. These applications can post information for you, and read and write information about your account. You may have authorized many applications to use Facebook or Twitter, but you don’t notice that hackers implant their own applications and you continue to use these applications.
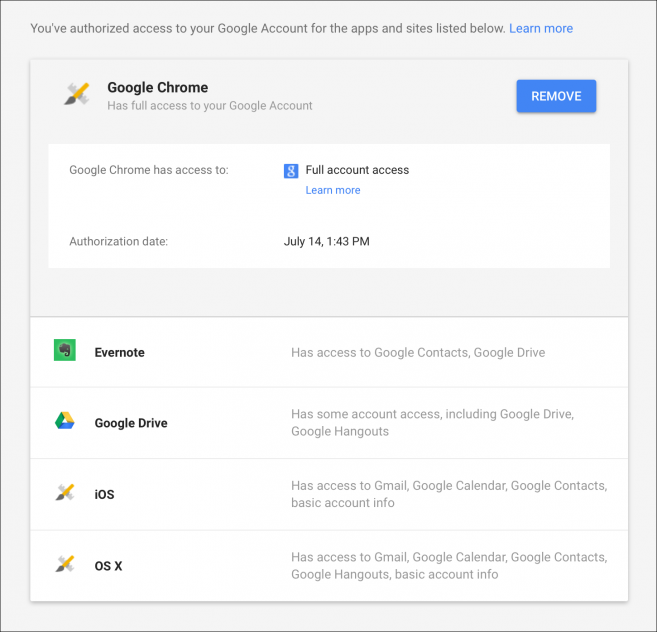
What to do if hacked? You need to check the social media platforms you use and. If you don’t recognize any authorized apps, revoke their access.
7. Delete Any Sensitive Data from the Hacked Account
Maybe it’s too late, but just in case, you had better delete all really sensitive data from the hacked account. It doesn’t mean they have browsed all your data or files, or have copied everything that they have access to your account.
Therefore, if you are concerned about any important files, especially those containing personal information, delete them immediately. This is especially true for services like Dropbox, Google Drive, and iCloud Drive. If you store important files on these cloud services, you should clear the folder right now.
Also see: Google Drive VS Dropbox: Which Is Your Best File Storage Choice
Now, you have known what to do if hacked.
Back up Your Data to Keep It Safe
In most cases, keeping a regular data backup is as important a step in seeking to protect against threats as strong passwords and antivirus software. Once your data get lost because of the hackers’ attack, you can use the backup to restore it.
In order to back up important data, you can choose to take a piece of third-party backup software – MiniTool ShadowMaker.
MiniTool ShadowMaker is a professional backup program that can be used to back up the operating system, disk, partition, file, and folder. In addition, it is a user-friendly program to provide protection for your computer and data.
To back up data, you can download MiniTool ShadowMaker Trial which can be used for free within 30 days from the following button.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Now, I will show you how to back up files step by step with pictures.
Step 1: Launch it to click Keep Trial and choose Connect in This Computer to continue.
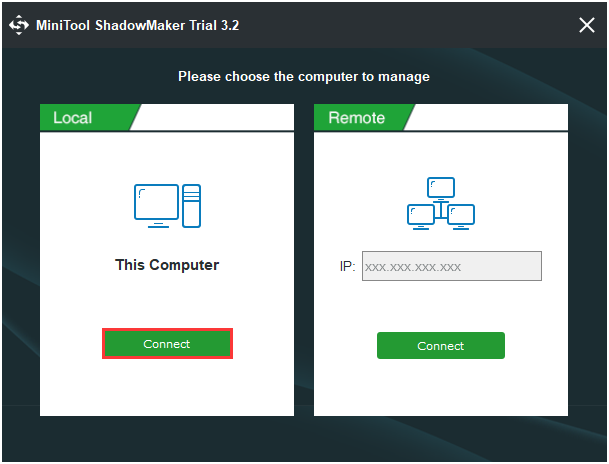
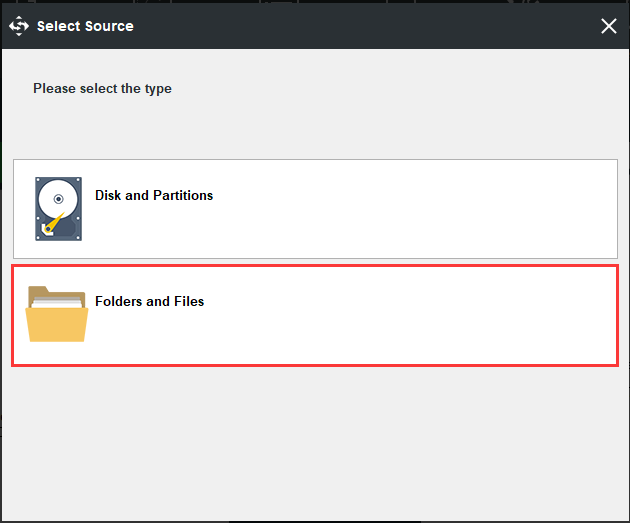
Step 2: After entering its main interface, go to the Backup page. Then click the Source module to choose the backup source. As for data backup, please choose Folders and Files to continue and choose the files you want to back up.
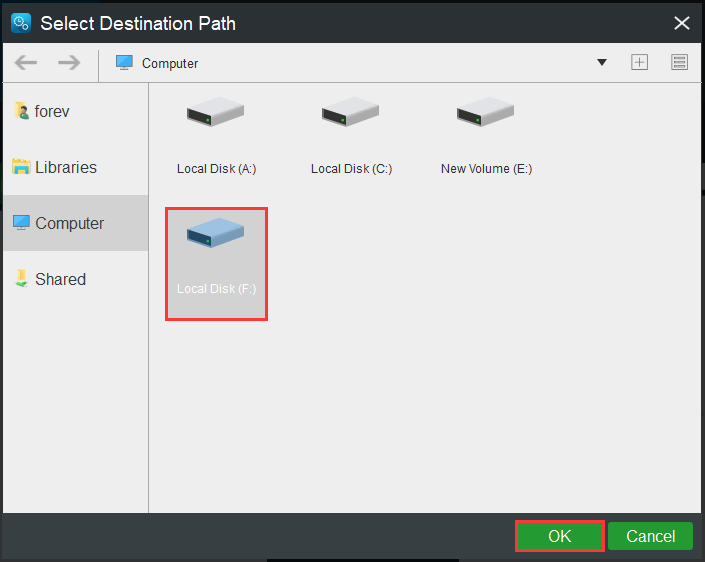
Step 3: Returning to the Backup page, click the Destination module to select the destination path so as to save the backup image. It is recommended to choose an external hard drive.
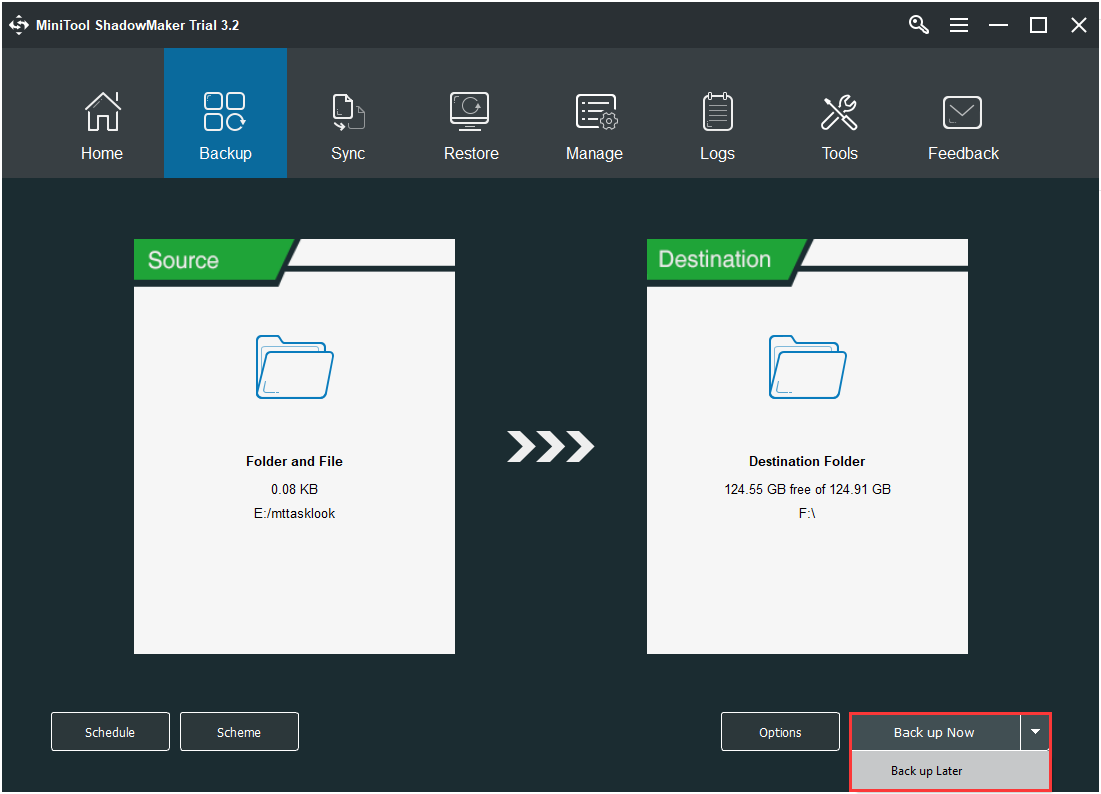
Step 4: After having successfully selected the backup source and destination, you can click Back up Now to perform the data backup action immediately. Or you can choose to click Back up Later to delay the process of the backup.
When the process is finished, you have successfully backed up files and have provided protection for the data. From the above information, you can see MiniTool ShadowMaker is a very easy and convenient tool.
Further Reading
It’s also recommended to use the Sync feature in MiniTool ShadowMaker. In this way, you can also provide protection for files. File synchronization is another form of backup which enables you to store files in two or more physical locations such as external hard drives, USB flash drives and so on.
Here is how to sync files:
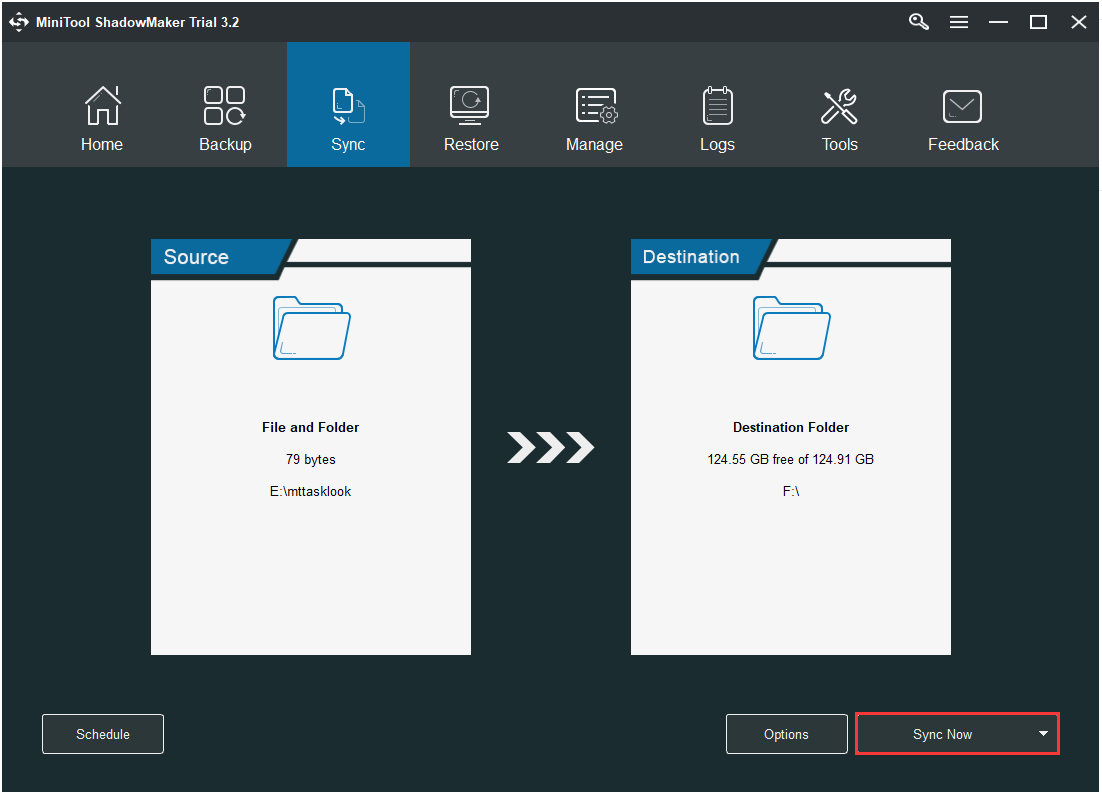
Step 1: After launching MiniTool ShadowMaker, go to the Sync page.
Step 2: Click the Source and Destination module to choose the files that you want to sync and the storage path.
Step 3: Click the Sync Now button to immediately perform the sync process.
Also see: 5 Useful Solutions to Sync Files Among Multiple Computers
Bottom Lines
In conclusion, you can know the hacking signs and what to do if you have been hacked from this post. I have also introduced how to back up data with MiniTool ShadowMaker to protect it on Windows 10.
In addition, if you have other suggestions for preventing the computer from hacking, share them in the comment zone. What’s more, if you have any problem with MiniTool ShadowMaker, please don’t hesitate to contact us via the email [email protected].

