This post shows you in-depth details about SCP protocol, including its definition, working principle, use, and some extra information. In a word, it provides you with a full introduction to SCP protocol.
Multiple tools and technologies can be used to transfer data between two laptops. However, you sometimes may get confused because of the wide selection of client programs and available protocols. This situation is more common for beginners.
When sending sensitive data that requires more than a simple transfer, you should consider methods with an appropriate level of security. Performing data transfer through SCP protocol is one of the methods, which is built for the secure transfer of digital information.
What is SCP protocol? To get the detailed information, keep reading this post of MiniTool.
What Is SCP Protocol
Secure Copy Protocol (SCP) is a method based on SSH for safely transferring computer files between a local host and a remote host or between two remote hosts. The SCP protocol is a file transfer network protocol.
However, OpenSSH developers claimed that SCP is outdated, inflexible, and not really effective in April 2019. What’s worse, SCP protocol is regarded as one of the scariest hacks and vulnerabilities of the year by ZDNet in 2019. Then newer protocols like SFTP and RSYNC are recommended.
With SCP, you can transfer files quickly by using the command line. This method often is faster and simpler than utilizing a client with graphical interface. What’s more, this command-line feature can also be used for automating batch files and scripts transfers.
The Secure Copy Protocol is cross-platform. Therefore, you can see versions and programs for standard operating systems such as Windows, macOS, Linux, Android, as well as iOS.
How Does SCP Protocol Work
Secure Copy needs authentication from involved hosts. Besides, you should set up an SSH connection between the local host and the targeted remote host before performing the transfer via the protocol. For that, you are required to enter the SSH login information or an authorized key for the public key authentication.
After building up the SSH connection between the two hosts, the SCP client will begin a secure copy process with two different available modes (source mode and sink mode). SCP clients often utilize the -f flag (from) to trigger source mode. If you want to trigger sink mode to transfer data to the targeted remote host, you need to use -t flag (to).
- Source mode: An SCP request in the source mode reads files from the targeted distant host and sends them back to the client.
- Sink mode: If the sink mode is used via the SCP protocol on the client, it will send signals to the remote host indicating that there is input data to be written to the remote host.
How to Use SCP
As mentioned above, SCP is supported by multiple operating systems and offers an excellent safety solution by including SSH. The combination features (authentication and encryption) of SCP protocol put it on par with the SFTP that utilizes the SSH mechanism too.
SCP has a faster transfer speed than SFTP. Hence, if you want to transfer files quickly and safely to a web server or when the sensitive data needs to be distributed in a local network, SCP is a great option.
Systems like macOS, Windows, as well as Linux have a standard embedded secure copy client called “SCP”. Hence, you can transfer data through SCP protocol by using the command prompt window or terminal.
To copy the source file into the specified directory on the target host with the user logged in via SSH using the name “test”, you need to use this command.
scp SourceFile test@host:directory/TargetFile
To transfer a file from a remote host to the local host participating in SCP, type the following command.
scp test@host:directory/SourceFile TargetFile
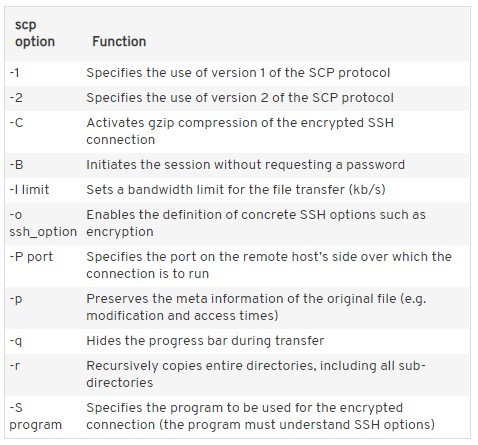
The above commands only show a simple process for copying without any additional options provided by SCP protocol. To add these options to the command, they should precede the file and host information as shown in the commands below.
- scp [option(s)] [SourceFile] [user@host:directory/TargetFile]
- scp [option(s)] [user@host:directory/SourceFile] [TargetFile]
You can refer to the table below to add other options.