Although Microsoft is constantly updating its operating system and releasing patches to maximize system security, bugs and vulnerabilities still occur now and then. Just now, a new vulnerability was discovered in the Windows Task Scheduler by a Twitter user.
On August 28, 2018, the Twitter user called SandboxEscaper posted new tweet, saying that there is a serious vulnerability in Windows Task Scheduler. By taking advantage of this vulnerability, the malware or malicious users are able to gain control of the system easily.
Vulnerability in the Windows Task Scheduler Was Discovered
Here is the alpc bug as 0day. I don’t fucking care about life anymore. Neither do I ever again want to submit to MSFT anyway. Fuck all of this shit.– Twitter user SandboxEscaper
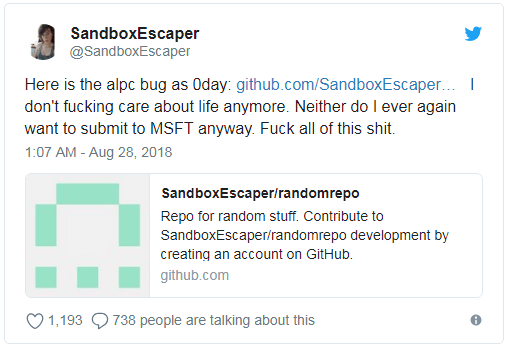
SandboxEscaper is claimed to be tired of IT security work. After revealing the vulnerability in Windows system, he or she also added that: Microsoft is stupid and I can’t wait to sell bugs in their software. And he or she linked to a page on GitHub containing a proof-of-concept (PoC) for the vulnerability.
Finally, SandboxEscaper deleted his or her Twitter account and claimed that he or she will be “gone” for a bit.
Local Privilege Escalation Bug Is A Headache
This bug occurs in the Advanced Local Procedure Call (ALPC) interface, which is a Windows mechanism aiming at improving the communication between a client process and a server process.

This local privilege escalation security flaw allows hackers to gain administrative access on Windows systems. So, the access of malicious code can be elevated easily by the hackers from a limited user role to an all-access system account.
That is to say, if you have downloaded and run a piece of malicious software, this software will gain access to privileges which are not supposed to be gained.
This vulnerability in Windows system is said to be caused by errors in the handling of ALPC systems. As I said before, the zero-day flaw allows local users to obtain system privileges. But, the impact is not so large since ALPC is a local system. Even though, disclosing this zero-day bug to the public is still a headache for the Redmond giant.
CERT/CC Analyst Confirms Windows Zero-day Exploit
Till now, there is no workaround for the vulnerability.
Will Dormann, the vulnerability analyst working at CERT/CC, have tested this flaw and then confirmed that it even exists in a fully-patched 64-bit Windows 10 system.
Afterwards, Will Dormann published a vulnerability note on CERT, declaring that the Task Scheduler of Microsoft Windows contains a local privilege escalation bug in the Advanced Local Procedure Call interface. This makes it possible for a local user to gain system privileges with negligible effort.
The CERT/CC is currently unaware of a practical solution to this problem, according to the vulnerability note.
Microsoft’s Response to the Zero-day Flaw
A spokesperson of Microsoft said that the company will make efforts to proactively update the impacted devices in a short time. The next round of patches of Microsoft is scheduled to be issued on Sept. 11. Therefore, users have to wait until then unless Microsoft finally decides to release a patch out of schedule.
Up to now, no one is said to be actually influenced by this vulnerability in the Windows Task Scheduler. However, the unpatched vulnerabilities can be scary, so I advise you not to forget to download the newest patch of Windows when it is finally released.