What Is a Firewall?
First of all, you should have a basic knowledge of the firewall. A firewall is a network security device that monitors incoming and outgoing network traffic and allows or blocks data packets based on a set of security rules.
The goal is to create a barrier between your internal network and incoming traffic from external sources, such as the Internet, to prevent malicious traffic like viruses and hackers. Maybe, you are interested in this post – Top 10 Anti Hacking Software to Protect Your Computer.
Nowadays, there are many types of firewalls and maybe you don’t know which one to choose. Thus, in the next part, I will introduce the detailed information about the several types of firewalls. You can know the advantages and disadvantages of each one. Then, you can know which one you should choose.
Different Types of Firewalls
- Packet-Filtering Network Firewalls
- Web Application Firewalls
- Unified Threat Management Appliances
- Network Segmentation Firewalls
- Cloud-Based Firewalls
- Database Firewalls
- Circuit-Level Gateways
- Stateful Multilayer Inspection Firewall
Types of Firewalls
What are the different types of firewalls? What are the 3 types of firewalls? These questions are often asked. Actually, there are 8 firewall types – packet-filtering network firewalls, web application firewalls, unified threat management (UTM) appliances, network segmentation firewalls, cloud-based firewalls, database firewalls, circuit-level gateways, stateful multilayer inspection firewall.
1. Packet-Filtering Network Firewalls
Packet-filtering network firewalls are also called traditional network firewalls. They help to prevent unwanted traffic from entering the corporate network to provide necessary network protection.
They apply a set of network firewall security rules to determine whether to allow or deny access to the network. The firewall simply checks packets passing through the router. The checked information includes destination and originating IP address, packet type, port number, and other surface-level information.
Advantages
- It doesn’t waste sources and doesn’t have a huge impact on system performance.
- It’s easy to implement by using permission and denial statements.
- Compared with the deep packet inspection technique, the CPU intensity is lower.
- It can be configured on almost every Cisco IOS.
Disadvantages
- It cannot mitigate IP spoofing attacks.
- The ACL is difficult to maintain as the size increases.
- It can’t implement filtering based on the session state.
2. Web Application Firewalls
Web application firewalls can protect web applications from various application-layer attacks, such as SQL injection, cross-site scripting (XSS), and cookie poisoning. You can stop a series of attacks designed to steal data by sabotaging the system with the correct web application firewall.
Advantages
- It can protect applications from port scanning.
- It is prone to security vulnerabilities and easier to patch.
Disadvantages
It can’t easily support all applications, and it will reduce the performance of protected applications for end-users.
3. Unified Threat Management Appliances
Unified threat management (UTM) appliances provide almost complete security solutions for small and medium enterprises. Typical UTM functions include traditional firewalls, intrusion detection systems, Internet gateway security, and URL blacklists.
Although most UTM can protect network security well, if you want to get better protection, you need the best-in-class solutions for each security function. If you don’t have dedicated security personnel and lack the skills required for configuration point solutions, UTM is a great choice for you.
Advantages
- It’s easy to use and convenient to manage.
- It can satisfy all of your demands after purchasing it.
- It can provide additional security services, but additional licensing fees need to be paid.
Disadvantages
It may not provide the same level of protection as a more complex product.
4. Network Segmentation Firewalls
Network segmentation firewall is also one of the firewall types. It is also called the internal network firewall, which is used to protect sites, functional areas, departments, or other business units by flowing network traffic. It can also be used to provide additional protection for network areas that need to be secured, such as databases or R&D units.
Advantages
If an attacker can access the network, the firewall may make it more difficult for them to access particularly sensitive data.
Disadvantages
It may cause performance and availability issues and may cause the failure of some network services.
5. Cloud-Based Firewalls
The cloud firewall provided as a service is configured and maintained by a security professional specializing in firewall management, so it can provide a very good level of protection for the assets it protects.
It can protect the network, applications, databases, and other IT resources. They are usually achieved by configuring corporate routers to divert traffic to cloud-based firewalls, while mobile users can connect to it through a VPN or use it as a proxy.
Related Article: How to Set Up a VPN on Your Windows 10 PC [Full Guide]
Advantages
- It is highly scalable.
- Multiple sites can be protected by it.
Disadvantages
Service providers are unlikely to keep up with the specific security requirements of their customers like insiders.
6. Database Firewalls
Database firewalls are a subset of web application firewalls. They are usually installed directly in front of the database server they protect. They are designed to detect and prevent specific database attacks. These attacks may lead attackers to access confidential information stored in the database.
Advantages
It monitors and audits database access and generates compliance reports for regulatory purposes.
Disadvantages
- They will only work if they are properly configured and updated.
- There are few protective measures against vulnerabilities.
7. Circuit-Level Gateways
Circuit-level gateways use another relatively fast method to identify malicious content. When they are established between the local and remote hosts, they monitor the TCP handshake and other network protocol session initiation messages on the network to determine whether the initiating session is legitimate.
Advantages
It can save sources.
Disadvantages
It doesn’t check the packet itself.
8. Stateful Multilayer Inspection Firewall
Stateful multilayer inspection firewalls combine packet inspection technology with TCP handshake verification. Compared with other firewalls, it can provide a higher protection level. Stateful inspections and firewalls that use this technology usually reject any traffic between trusted and untrusted interfaces.
Advantages
- It helps in filtering unexpected traffic
- It can be implemented on a broad range of routers and firewalls
- It can help migrate denial of service (DDOS) attacks.
Disadvantages
- It can’t mitigate application-layer attacks.
- Expect for TCP, other protocols do not have well-defined state information to be used by the firewall.
- Some applications may use more than one port for successful operation.
Which One Should You Choose
No matter how powerful the firewall is, there is no single layer of protection enough to protect your business. Your network should have multiple layers of firewalls on the periphery and separate different assets on the network to provide better protection.
The specific firewalls that you want to use are depending on the capabilities of the network, the relevant compliance requirements of the industry, and the resources used to manage these firewalls. Thus, before choosing the firewall, you should conduct a security policy review and evaluation.
Now, you have known the types of firewalls and which one you should choose.Click to Tweet
A Firewall Alternative to Protect Your Computer
In addition to these different types of firewalls, a great backup software – MiniTool ShadowMaker is also a powerful tool to protect your Windows. It is an all-around and free backup software designed for Windows 10/8/7, providing you with a data protection & disaster recovery solution.
Besides backing up the system, this software can also be used to back up files, folders as well as the partitions. It is also a clone tool that can help you to clone the OS from HDD to SSD without data loss. So, besides creating a system image, you can also choose to clone the OS disk to another hard drive to get the Windows system without reinstalling.
MiniTool ShadowMaker also supports restore Windows backup to a different PC with dissimilar hardware. This post – How Can You Do Windows Backup Restore to Different Computer can help you do that.
Now you can download and try MiniTool ShadowMaker Trial Edition to do the backup task.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Let’s see how to use MiniTool ShadowMaker to back up your files.
Step 1: Decide a Backup Mode
- Launch MiniTool ShadowMaker.
- Continue to use the trial edition by clicking Keep Trial.
- Choose This computer to continue by clicking the Connect button.
Step 2: Choose the Backup Source
- Under the Backup page, click Source to choose the backup type – Folders and Files.
- Select the files you need to back up and click OK.
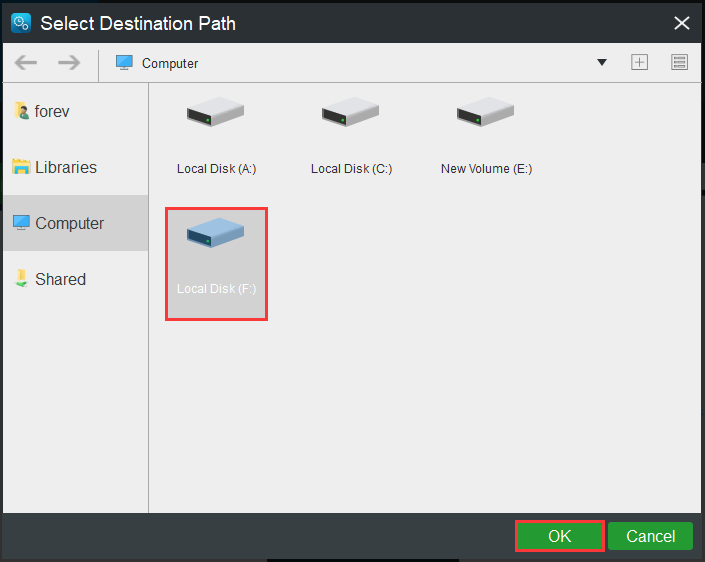
Step 3: Choose a Destination Path
- Click the Destination tab.
- Choose one partition to store your files based on your needs and click OK.
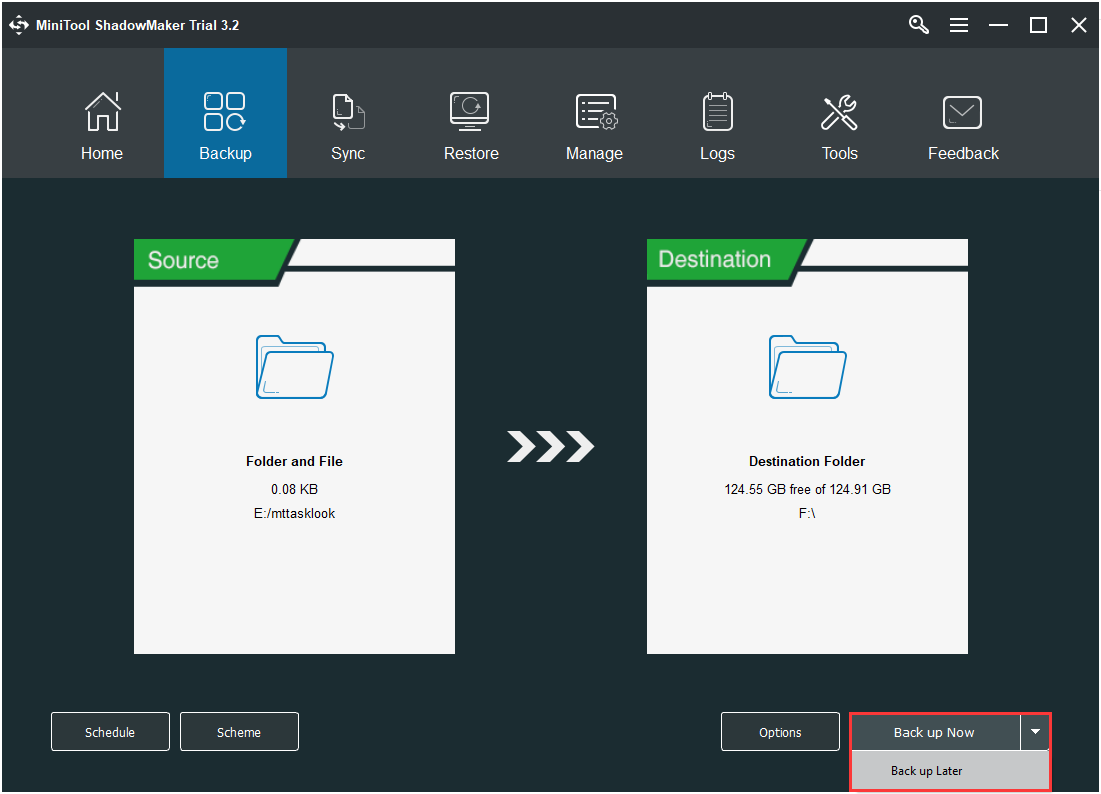
Step 4: Start the Backup Process
- Go back to the previous interface.
- Click Back up Now to start the process immediately or choose Back up Later to delay the backup task.
Now, you have backed up your important files successfully.
You can use another feature of MiniTool ShadowMaker to back up files: Sync. Here is how to sync files:
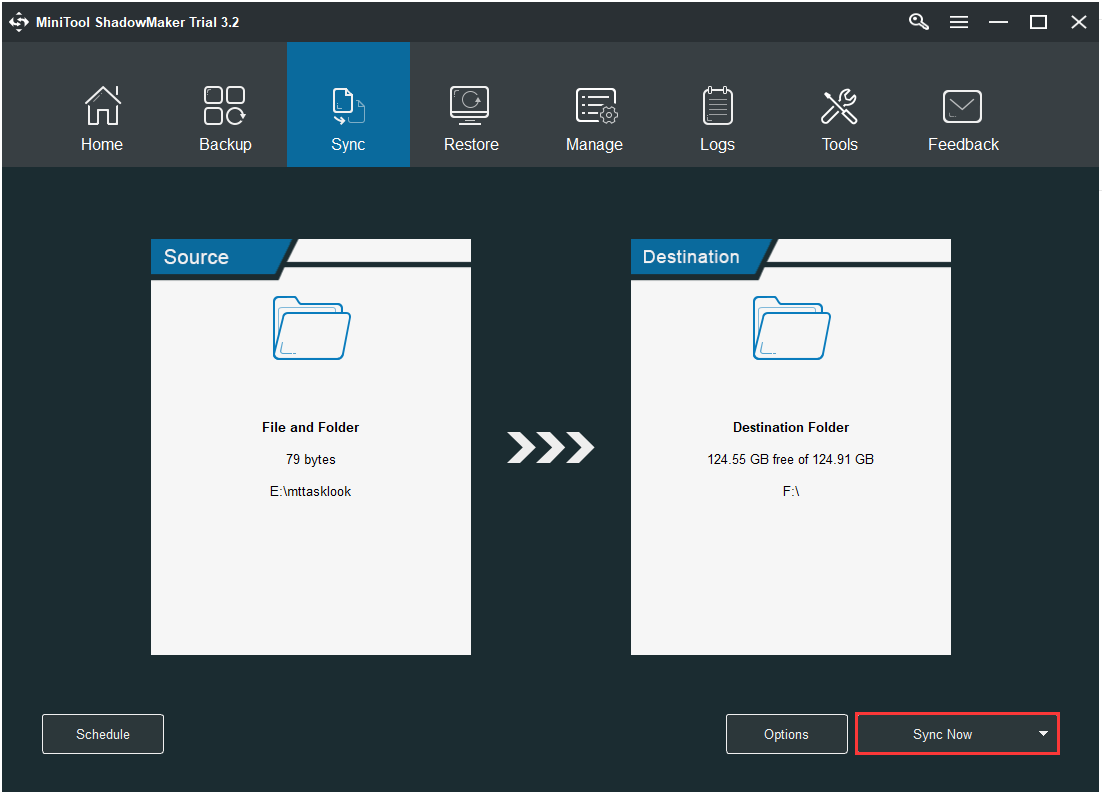
Step 1: After launching MiniTool ShadowMaker, go to the Sync page.
Step 2: Click the Source and Destination module to choose the files that you want to sync and the storage path.
Step 3: Click the Sync Now button to immediately perform the sync process.
Also see: 5 Useful Solutions to Sync Files Among Multiple Computers
Bottom Line
This post has briefly shown you what firewall is and the different types of firewalls. Besides, this post also introduces you to a powerful program – MiniTool ShadowMaker, which can help you back up data to protect it.
If you have any problems when you are using our program, please let us know. Or if you have any suggestions, also tell us. Sending an email to [email protected] or leaving a comment below is available.
Types of Firewalls FAQ
Here are some tips for you to kill a firewall.
- Use a web-based proxy.
- Use a VPN.
- Use remote access to your PC.