What Is MyDoom?
MyDoom, also called W32.MyDoom@mm, Mimail.R, Shimgapi, or Novarg, is a kind of computer virus that affects the Microsoft Windows operating system (OS). It was first seen on January 26th, 2004. Exceeding previous records set by the ILOVEYOU and Sobig, MyDoom virus became the fastest-spreading email worm ever, a record that as of 2021 has yet to be surpassed.
MyDoom was named by Craig Schmugar, an employee of McAfee computer security company. He was also one of the earliest discoverers of the virus. Craig selected this name since he noticed the text “mydoom” within a line of the MyDoom source code. “It was evident early on that this would be very big. I thought having ‘doom’ in the name would be appropriate”, said Craig.
Who Created MyDoom?
MyDoom worm appears to have been commissioned by email spammers to deliver junk e-mails via infected computers. The spam contains a text message “andy; I’m just doing my job, nothing personal, sorry”, leaving a lot of people believing that the malware’s creator was paid to work.
Initial analysis of Mydoom suggested that it was a variant of the Mimail virus, so there is an alternate name of MyDoom called Mimail.R. That prompts speculation that the MyDoom computer virus was created by the same author as the virus Mimail. Later analyses were less conclusive as to the link between the two viruses.
Speculative early coverage thought that the main purpose of MyDoom was to perpetrate a distributed denial-of-service (DDoS) attack against SCO Group. Around 25% of Mydoom.A-affected computers targeted SCO Group with a flood of traffic.
Trade press conjecture, spurred on by SCO Group’s own claim, said that this meant the malware was created by a Linux or open-source supporter in retaliation for SCO Group’s controversial legal actions and public statements against Linux.
However, this theory was rejected immediately by security researchers. Since then, it has also been rejected by law enforcement agents investigating the worm, who attribute malware MyDoom to organized online crime gangs.
How Does MyDoom Spread?
MyDoom is mainly transferred through email, appearing as a transferring error with subject lines containing “error”, mail transaction failed”, “test” or “mail delivery system” in different languages, such as English and French.
The email is attached with a file that, if executed, resends the virus to email addresses found in local files like a user’s address book. It also copies itself to the “shared folder” of peer-to-peer file sharing application Kazaa in an attempt to spread that way.
Smartly, MyDoom avoids attacking email addresses of certain universities including Stanford, UC Berkeley, Rutgers, and MIT, as well as certain companies such as Symantec and Microsoft. Some early reports held that the virus avoids all .edu addresses, but it’s not true.
The initial version MyDoom.A is thought as carrying 2 payloads. One is a backdoor on port 3127/TCP to enable remote control of the infected computer by putting its own SHIMGAPI.DLL file in the system32 directory and opening it as a child process of Windows Explorer. This is essentially the same backdoor as what was found in Mimail.
The other is a denial-of-service attack against the website of the controversial company SCO Group, timed to commence February 1st, 2004. Yet, not a few virus analysts doubted whether the payload would actually work or not. Later test shows that it functions in only 25% of affected systems.
The second version MyDoom.B, carrying the same payloads as the initial version A, also targets the Microsoft website and blocks access to Microsoft websites and popular online antivirus sites. It modifies the hosts file to block antivirus programs as well as their updates. The smaller number of copies of MyDoom version B in circulation means that Windows servers suffered few damages from the B version.
MyDoom Virus History / MyDoom Virus Effect
Below is the timeline of the MyDoom Virus event.
January 26, 2004,
MyDoom was first identified at about 8 AM EST (1300 UTC), right before the starting of the workday in North America. The earliest emails originated from Russia. After a few hours until the noon of the day, the virus’s fast spread slowed down overall Internet performance by around 10% and average web page load times by approximately 50%. It was reported that MyDoom malware was responsible for about 10% of email messages then.
Although the denial-of-service attack was scheduled to begin on February 1st, 2004, SCO Group’s website went offline briefly in the hours after the virus was first released. Whether MyDoom itself was responsible for this or not is unknown.
January 27, 2004
SCO Group provided a 250 thousand US dollars reward for information related to the designer of MyDoom. In the United States, the FBI and the Secret Service started investigating the virus.
January 28, 2004
Mydoom.b was discovered. The first message sent by it was identified at about 1400 UTC and also appeared to originate from Russia. The new version included the original denial-of-service attack aimed at SCO Group and an identical attack against www.microsoft.com starting on February 3rd, 2004.
Yet, both attacks are suspected to be either broken or non-workable decoy code intended to conceal the MyDoom exploit. MyDoom.B also prevented access to the sites of more than sixty computer security firms and pop-up advertisements offered by online marketing companies like DoubleClick.
On this day, the spread of MyDoom was at its peak. Security companies reported that MyDoom was responsible for approximately 20% of emails that day.
January 29, 2004
The spread of MyDoom began to decrease as bugs in the source code of version B of Mydoom prevented it from spreading as fast as first anticipated. Microsoft offered a $250,000 reward for information leading to the arrest of the creator of MyDoom B.
February 1, 2004
An estimated 1 million computers in the world infected by MyDoom began the worm’s massive distributed denial-of-service attack, the largest such attack to date. On this day, the virus arrived in Australia and East Asia. SCO removed www.sco.com from the DNS around 1700 UTC on January 1st.
February 3, 2004
The virus’s denial-of-service attack on Microsoft began, for which Microsoft prepares by offering a website that wouldn’t be affected by the virus, called information.microsoft.com. Luckily, MyDoom virus damage remained minimal and microsoft.com remained functional during the attack.
That was attributed to the comparatively low distribution of the MyDoom.B variant, the high load tolerance of Microsoft website servers, and preparation taken by Microsoft. Some experts stated that the burden during the virus attack is less than that of Microsoft software updates and other such web-based services.
February 9, 2004
Doomjuice, a “parasitic” virus, began spreading. It made use of the backdoor left by MyDoom to spread. Doomjuice didn’t attack non-affected machines. Its payload, similar to one of MyDoom.B’s, is also a denial of service aiming at Microsoft.
February 12, 2004
MyDoom.A is programmed to stop spreading. Yet, the backdoor remains open after this date.
March 1, 2004
MyDoom.B is programmed to stop spreading. Similar to MyDoom A, its backdoor remains open.
July 26, 2004
Another variant of MyDoom attacks Google, Yahoo, Lycos, and AltaVista, completely stopping the function of the Google search engine for the larger portion of the workday and creating noticeable slow-downs in the AltaVista and Lycos engines for hours.
September 10, 2004
The version U, V, W, and X of MyDoom appeared, spreading worries about a new and stronger MyDoom was being prepared.
February 18, 2005
MyDoom version AO appeared.
July 2009
MyDoom resurfaces in the July 2009 cyber-attacks affecting South Korea and the USA.
2019
15 years later, the fastest spreading and most destructive computer virus MyDoom still persisted and it was used in phishing attacks. According to an analysis by Unit 42, 1% of all e-mails containing viruses sent during 2019 have been MyDoom emails. The vast majority of IP addresses distributed MyDoom in 2019 are in China, the US, and the UK.
How to Prevent MyDoom from Spreading?
According to the timeline of the MyDoom virus, you can figure out that there are probably still MyDoom infections in the world. Maybe someday you will receive an electronic mail letter from your friend containing the worm. If you open the attached file without knowing it is a virus, the attack will execute and copies will be sent to your contacts… Maybe it will result in another global attack…
Horrible, right? Then, you must want to know how to prevent MyDoom from spreading out from you once you receive it. Here, some tips are recommended to you.
Tip 1. Always Keep Antivirus Open
I believe most of you have at least one security program installed on your computers. At least, each Windows OS is equipped with a firewall Windows Defender. All you need to do is to keep it on while using your machine. Then, if you happen to receive an email containing a virus, the firewall will probably stop you from opening or downloading it to your local storage by sending you a warning message.
Tip 2. Never Open Unknown Files
You’d better never open unknown files. If you receive a file that you don’t know, try your best to first figure out what it is, especially whether it is safe or not, before you finally open it. If the file is attached to the email sent to you by one of your contacts, you can reply to ask for what it is before downloading it to your machine. If the file is confirmed to be safe and clean, you can open it; if it’s not, just completely delete the email together with the attachment.
Tip 3. Regularly Scan Computer for Virus
To only check for newly received files is not enough! Some viruses may have hibernation and they will attack your system usually a few days later since they get on your machine. So, you are suggested to scan and have a full check of your entire computer in case of potential risks relying on security software. And, you should do the process regularly and frequently since you never know when the hibernated virus will wake up.
Tip 4. Don’t Forget to Back up Important Files
Though MyDoom only slows down your computer performance and block you from accessing some online services/websites, it is still helpful to make a backup of your crucial and frequently used files. Once you have a backup of them, if you are influenced by MyDoom in one of your devices, you can restore those files to another healthy device and continue your work.
Also, if you are infected by ransomware like NotPetya and WannaCry, your original files will be encrypted, destroyed, or deleted. Anyhow, you can’t access them. Then, if you have a previous backup of those items, you can restore them to another computer and reduce your data loss.
Then, how to create a backup of important files and folders? You can just copy and paste them to a safer place, but it requires the same amount of storage space as the source files. If you have lots of files to be backed up, or if you plan to back up your system, large storage space is needed.
You can also rely on Windows built-in features and utilities. Yet, they are somehow complicated to operate and lack some popular and useful functions. Thus, they can’t satisfy users’ needs.
Fortunately, there are professional and reliable third-party applications that can back up files/folders, systems, hard disks, partitions/volumes, etc. based on customers’ special needs. They are specialized in schedule backup, backup with schemes (saving storage space), and many other backup options.
One of such excellent backup programs is MiniTool ShadowMaker. It can quickly back up your family photos/videos, favorite songs, work documents, customized operating system, and so on. To use it, first of all, download and install it on your device. Then, follow the below guide to create an initial backup of import files.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 1. Launch MiniTool ShadowMaker and click Keep Trial on its first screen.
Step 2. Then, it will enter its main interface. There, click Backup in the top tab menus.
Step 3. In the Backup tab, click the left module to select the source files you want to back up.
Step 4. Click the right module to select a destination for saving the backup image.
Step 5. It will redirect you to the Backup tab and display the preview of the backup task. Have a check of the task and confirm it by clicking Back up Now in the lower right.
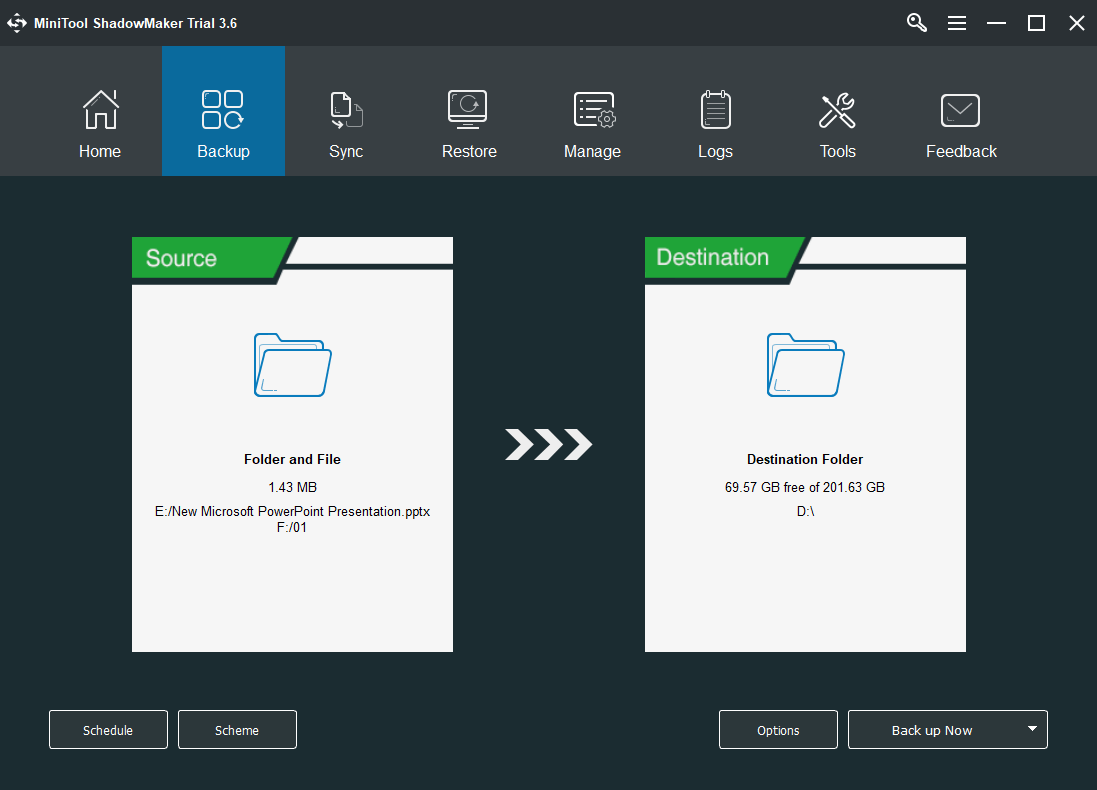
It will start to back up your important files. Just keep your computer on during the process. You can also create a schedule to automatically back up those files in the future by clicking the Schedule button in the lower-left before executing the initial backup. Or, you can customize your own backup scheme to save your disk space by clicking Scheme in the lower left.
OK, that’s all related to the MyDoom virus. If you have something to share with our readers about MyDoom or other computer viruses, just write it in below comment zone. Or, if you encounter any problem while using MiniTool ShadowMaker, just contact our support team at [email protected].
![[Answered] Is Vimm’s Lair Safe? How to Use Vimm’s Lair Safely?](https://images.minitool.com/minitool.com/images/uploads/2021/02/is-vimms-lair-safe-thumbnail.jpg)