This article posted by MiniTool party elaborates on malware detection and removal with its definition, necessity, and techniques. It also discusses malware prevention and detection with malware removal tools and a backup program to keep data safe.
What Is Malware?
In general, malware is a kind of malicious and harmful software that infects your device (computers or smartphones) and destroys your data or operating system (OS). Sometimes, it pretends to be a legitimate application before finally attacking your machine.
Malware can get into your device in multiple methods. Usually, it will cheat users in the way of malicious links, harmful files, phishing emails with infected attachments, fake installers, and so on.
Once arrived at your machine, in most cases, the malware will hide itself firstly. Then, it will penetrate your computer files, folders, apps, or locations one by one. Finally, it will get into the core of your machine – the OS and carry out attacks.
For a powerful malware, it may directly access your system, record your personal info, and encrypt crucial data immediately after getting into your PC, without latency.
What Is Malware Detection?
Generally, malware detection is the process of scanning a target device or files to find malware. It is created specifically against malware. Relying on many techniques and tools, malware detection is reliable and effective.
Instead of a simple one-way process, malware detection is more complex than it seems to be. Yet, it won’t take long to complete a detection process of malware. Usually, it costs no longer than several minutes to finish a detection, and sometimes together with malware removal.
Why Need Malware Detection?
Due to the popularity and destructiveness of malware, it is of great necessity and importance to detect malware before it starts to attack its hosts or when it tries to infiltrate the computer. Once malware is detected, a warning message will be sent and received by users.
Therefore, the users will stop diving deeper into the insecure website or downloading unknown files. Thus, it will effectively keep hackers from controlling your device and stealing your information.
Types of Malware Detection
There are many kinds of malware detection methods. Some of them are popular now, some of them are well-known in the past, while some of them will become the trend in the coming future. Let’s learn them all and have a thorough understanding of the history of malware detection techniques.
#1 Signature-based Malware Detection
This type detects malware using antivirus (AV) programs that identify and block threats. Each file on the target computer is analyzed, assigned a signature or hash, and added to the signature database. The signature database is used to compare subsequent malware incidents.
When a file is found suspicious, the antivirus will look for patterns that match a known malware. If a match is found, the file will be blocked, isolated, or removed.
Signatures were the mainstay of malware detection technologies for many years. And, they are still useful for detecting known threats. However, when new unknown malware attacks, signatures can help little.
Today, signature-based detection is no longer an effective way due to constantly evolving malware. modern malware takes advantage of multiple new techniques to escape from detection. This makes it harder to find the malware by matching its signature with known malware.
Technologies have taken by modern malware:
1. Polymorphism
Polymorphic malware changes its features all the time to prevent being detected. Its creators make use of polymorphism to evade pattern-matching checking of antivirus tools. Employing a mutation engine, polymorphic malware can alter certain features like file names and hashes, thus hiding its malicious code.
Nowadays, most malware programs adopt polymorphism to change their signatures each time they iterate. So, these variants are undetectable by signature-based malware detection even they are based on known malware families.
2. Code Obfuscation
Obfuscation of code is another way used by modern malware to avoid detection. It makes it difficult to understand or even read malware source code thus bypassing static antimalware (AM) apps. Multiple methods are used to hide harmful code, such as packing to compress malware, encrypting malware, inserting dead code to change the appearance of the malware, and make instruction changes.
3. Abuse of Legitimate Signed Windows Binaries
Already signed binaries or components may be used to execute malicious code inside legitimate processes by hackers to evade signature-matching software. Therefore, using legitimate tools in suspicious processes is an indication of malware infection.
Since signature-based analysis is less effective than before, new advanced malware detection techniques must be created and they are.
#2 Sandbox
Sandbox technology detects malware by testing potentially malicious code in an isolated virtual environment. Within such an environment, researchers can observe the code’s real behavior and figure out its real intentions while malware can’t spread or carry out any damage to the system or network.
Yet, sandboxing has some shortcomings. In response to the sandbox technique, malicious inventors create malware that can figure out when it is running in a sandbox. If so, the malware will act in a legitimate way without harming the computer, which is different from its actual behavior when it’s running in the real environment.
Besides, some malware variants are designed to exploit the vulnerabilities of sandboxes. What’s more, this behavior-based malware detection sets some challenges to its application like costing much time.
#3 Heuristic Analysis
Heuristic analysis observes the behavior of a system or program to find new threats that aren’t detected by signature-based methods. Heuristic analysis establishes a baseline of normal activity for the system or software. Then, if something different happens, it will be regarded as a potential threat by heuristic analysis.
Heuristic analysis is one of the few technologies that are able to detect polymorphic malware. Moreover, it enables antivirus developers to continuously change baseline based on new-found threats while doesn’t give details on how threats are flagged to malware creators. So, hackers can’t update their malware accordingly.
Also, heuristic analysis has drawbacks. One of its disadvantages is that it is useless for malware whose code is sufficiently obfuscated.
Many malware detection apps have already adopted heuristic analysis technology including Avast and AVG. Avast malware detection has found some malicious threats using this technique like Win64:Malware-Gen, Win32:Trojan-Gen, Win32:Dropper-Gen, Win32:Malware-gen, Trojan.Win32.Generic, Win32:MdeClass, etc.
Since both heuristic analysis and sandboxing have cons, it is not enough to only rely on them (plus the old signature-based detection) to fight against today’s malware. Newer and more advanced technologies are needed. Therefore, several next-generation antivirus (NGAV) techniques have come into being.
#4 Endpoint Detection and Response (EDR)
EDR monitors and records data and events from endpoint logs and packets. The collected data is used to analyze what happens after malware infects your computer, look for IOCs to known malware activities, and help researchers to identify and respond to threats.
#5 Whitelist of Apps
The next solution to detect malware is whitelisting, which validates and controls all aspects of what a process is allowed to do and blocks programs from doing anything except what they are supposed to do. It is very useful to deal with threats like zero days.
However, the whitelist frustrates end users by preventing them to run completely safe applications. Thus, whitelist tech is only recommended in high-risk environments.
#6 Machine-Learning Static Analysis
This machine learning malware detection trains computers to recognize and differentiate between malicious and benign files. It teaches PCs what is bad and what is good so as to, eventually, the machines can sort the files on their own.
This machine or AI-learning-based technology takes different behaviors and calculates them into a conclusion on the nature of the file. Those behaviors include how long a file needs to open, file traffic, file daily behavior…
Though being intelligent and highly automatic, machine learning isn’t perfect to detect malware. Vice versa, this methodology can be exploited by hackers to train computer learning systems to misclassify malware samples as secure programs.
Moreover, machine or AI learning is a whole new technology not only in the computer field but also in other electronic fields. Therefore, it can’t be used solely for malware detection. Instead, it is recommended that utilize machine learning together with other mature or traditional detection technologies.
How to Tell Whether My Computer Is Infected by Malware or Not?
The above malware detection methodologies are somehow sophisticated for general users. Then, the following are some common symptoms if you are infected with malware.
- Slowing down computer performance
- Disturbing ads everywhere
- Secret disk space loss
- Abnormal system Internet activity increase
- Antimalware not working
- Inaccessible Files or computer
- System crash
Common Malware Types
Taking advantage of those malware detection technologies, nowadays, we have a list of common malware types. Below just lists the common malware types.
1. Virus
A type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. It requires a host program and can cause great damage. Some examples are Creeper, Conficker, Mirai, Win32/Simile, Gammima, and CiaDoor.
2. Ransomware
A type of malware from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. Some examples are CryptoLocker, Mercury, WannaCry, Ryuk, PXJ, Sodin, and Petya.
3. Spyware
A kind of software with malicious behavior that aims to gather info about a person or organization and send the info to another entity in a way that harms the user. An example of spyware is CoolWebSearch (CWS).
4. Adware
It is usually called advertising-supported software by its developers. Adware is software that generates revenue for its developer by automatically generating online advertisements in the software user interface or on the software installation screen. Some well-known apps or services support advertising including Adblock Plus, Skype, Gmail, and Facebook.
5. Potentially Unwanted Program (PUP)
Also called potentially unwanted application (PUA), PUP is software that a user may perceive as unwanted. It is usually bundled with a wanted program. Antivirus companies define the bundles as potentially unwanted programs that can include software displaying intrusive advertising (adware) or tracking user Internet to sell info to advertisers (spyware). Additional web browser toolbars, search bars, browser redirects, shopping helpers, weather apps, etc. all can be a PUP.
6. Worm
It is a standalone malware computer program that replicates itself to spread to other computers. Unlike a virus, it doesn’t need a host program. Some examples are ILOVEYOU, Stuxnet, SQL Slammer, and Mydoom.
7. Trojan
A trojan horse can be any malware that misleads users of its true intent. Usually, it spreads by some form of social engineering. The detected trojans include but are not limited to DarkComet, Zeus, Zlob, Dyre, and MEMZ.
8. Rootkit
A rootkit is a collection of computer software, usually malicious, designed to enable access to a computer or an area of its software that isn’t otherwise allowed and often masks its existence or the existence of other software. For example, Stoned Bootkit and Alureon (aka TDSS) are both rootkits.
9. Backdoor
Typically, a backdoor is a covert method of bypassing normal authentication or encryption in a computer, product, embedded device, or its embodiment. Trojan can be used to create vulnerabilities in a device and install a backdoor. Some examples are Sobig, Mydoom, Sony/BMG rootkit, and OpenSSL RSA.
10. Keylogger
Also known as keystroke logging or keyboard capturing, it is software or hardware that secretly records the keys struck on a keyboard. Keylogger is often used to steal passwords or other confidential info. Some keyloggers are Blue Kill, Zeus, SpyEye, Inputlog, Scriptlog, Translog, and FlashCrest iSpy.
11. Exploit
An exploit is a piece of software, a chunk of data, or a sequence of commands that uses a but or vulnerability to cause unexpected or unanticipated behavior to occur on computer software, hardware, or something electronic. Some well-known computer exploits are Rig, GreenFlash Sundown, Fallout, Magnitude, GrandSoft, and Zero-day.
12. Cryptojacking
Cryptojacking is a kind of malware that infects computers to use them to mine cryptocurrencies (Bitcoin or Monero) usually without users’ knowledge. So, it can also be called cryptomining. Cryptojacking can result in computer slowdowns and crashes due to straining of computer resources. Many known cyberattacks are cryptojacking like Coinhive, Kobe Bryant wallpaper, MyKings botnet, Outlaw botnet, Vivin, and Tesla cryptojacking.
13. Malvertising
Malvertising is the usage of online advertising to spread malware. typically, it injects malicious or malware-laden advertisements into legitimate online advertising networks and webpages.
14. Crimeware
Crimeware is a class of malware developed especially to automate cybercrime. It is designed to perpetrate identity theft through social engineering or technical stealth to access a user’s financial and retail accounts to take funds or carry out unauthorized transactions. An example of crimeware is Bankash.G trojan.
15. Bots
An Internet bot, web bot, robot, or simply bot, is a computer program that runs tasks (scripts) over the Internet. Some bots are good while others are used to launch malicious attacks.
A spambot is a software application designed to assist in the sending of spam.
Spybot worm is a large family of computer worms of varying characteristics.
Agobot, also known as Gaobot, is a family of computer worms whose variants surpass the variants of the Spybot family.
16. Bundled software
Bundled software, also called pre-installed software, is software that is already installed and licensed on a computer or cellphone from an original equipment manufacturer (OEM). Unwanted bundled software, also called bloatware or crapware, can include major security vulnerabilities.
17. Stealware
Stealware is a type of malware that covertly transfers data or money from its original owner to a third party. It uses an HTTP cookie to redirect the commission ordinarily earned by the site for referring users to another site.
18. Stalkerware
Stalkerware is monitoring software or spyware used for stalking. It is mostly used in smartphones. Some examples are Monitor.AndroidOS.MobileTracker.a, Monitor.AndroidOS.Cerberus.a, Monitor.AndroidOS.Nidb.a, Monitor.AndroidOS.PhoneSpy.b, and Monitor.AndroidOS.XoloSale.a.
Malware Detection Tools
After learning so much about the analyzing and detecting of malware, now, it’s time to talk about the removement of malware.
All above malware detection techniques need to be embedded into a malware detection tool to be available. And, such a tool is the same one that allows you to remove the detected malware. That is to say, you use a single tool to detect and remove malware.
Below are some powerful and famous brands of malware detection apps:
- Avast
- AVG
- Avira
- Bitdefender
- Cynet
- Emsisoft
- F-Secure
- HitmanPro
- Kaspersky
- LifeLock
- Malwarebytes
- McAfee
- Microsoft Windows Defender
- Norton
- PC Matic
- Restoro
- Sophos
- Trend Micro
- Viper
- Webroot
Many of the above programs are malware detection free or have free versions. There is no best malware detection software, only the most proper one. Just choose the one that suits you and satisfies you.
Besides those offline malware detection programs, there is also online malware detection like malware detection websites. They together carry out Microsoft malware detection, Windows 10/11 malware detection, external hard drive malware detection, network malware detection, etc.
How to Protect Your Computer from Malware?
In addition to antivirus programs or firewalls, you can defend your data in another way, which is creating backups. Another copy or more copies give double insurance to crucial files. To make a backup of your digital data, you’d better rely on a reliable and powerful tool like MiniTool ShadowMaker, which enables you to not only back up your files/folders, but also system, partitions/volumes, and even the entire hard disk.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
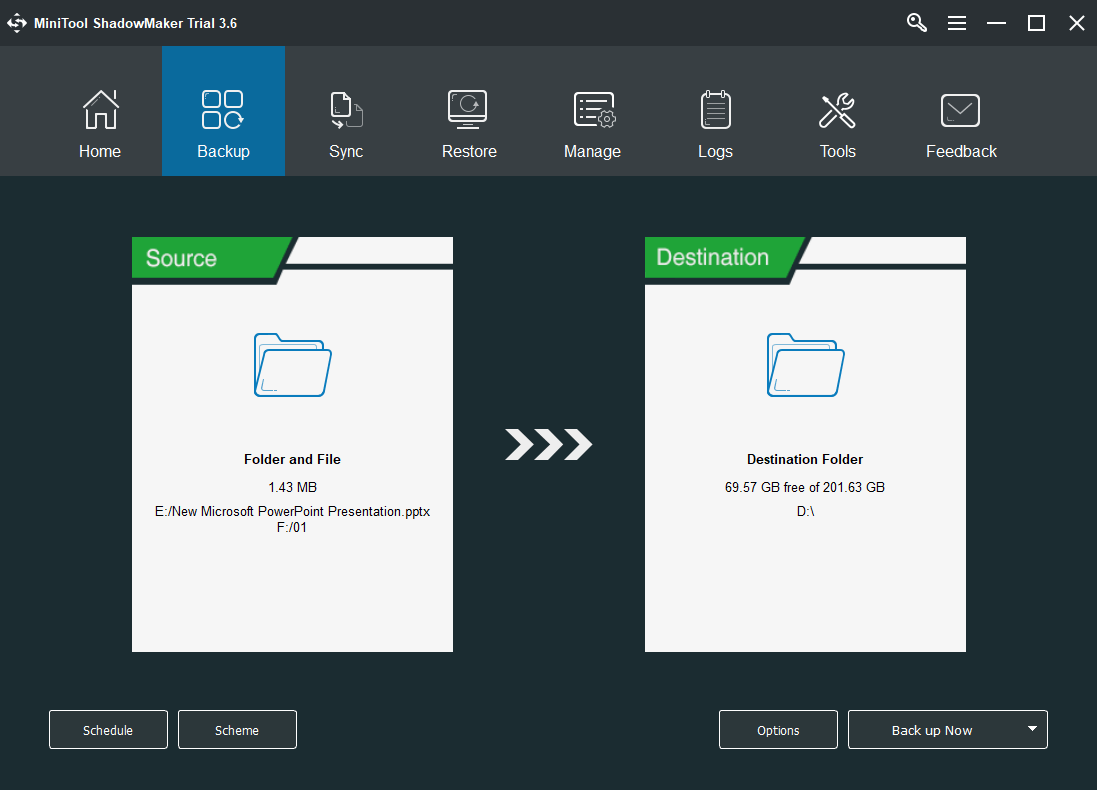
Also, MiniTool ShadowMaker allows you to create a schedule to automatically back up items daily, weekly, monthly, or on a special event in the future. As for backup types, it provides full backup, incremental backup, and differential backup; as well as the way to manage backup images.
Conclusion
Malware is always changing and evolving; there is never an almighty solution to detect and defeat it. What malware detection software should do is to keep up with the change of threats or attacks and work out correspondingly effective methodologies. Generally, such methods contain multiple protection layers and levels to detect and beat viruses.


![[Review] Fileless Malware: Definition/Detection/Affect/Removal](https://images.minitool.com/minitool.com/images/uploads/2021/04/fileless-malware-thumbnail.jpg)


![[Wiki] Microsoft System Center Endpoint Protection Review](https://images.minitool.com/minitool.com/images/uploads/2021/05/system-center-endpoint-protection-thumbnail.png)



![[Complete] List of Samsung Bloatware Safe to Remove](https://images.minitool.com/minitool.com/images/uploads/2021/05/list-of-samsung-bloatware-safe-to-remove-thumbnail.png)
